|
Public Key Infrastructure @@
|
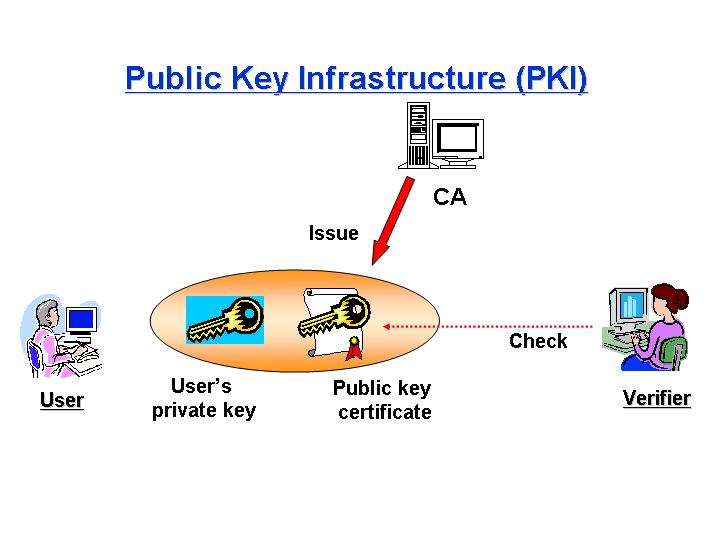
A Public Key Infrastructure (PKI) is the basis of security infrastructure whose services are implemented and provided using public-key techniques. Most of the protocols for secure e-mail, web service, virtual private networks, and authentication systems make use of the PKI. In a PKI, public-key certificates are used to bind an entity's identity information with the corresponding public-key. When the certificate is issued, its validity is limited by a pre-defined expiration time. Nevertheless, certificates are revoked in case of breaking that binding before its expiration date. Thus, the certificate verifier must check not only the expiration date on the certificate but also the revocation information of it.
Certificate revocation systems can be implemented in several ways. The most well-known method is to periodically publish a Certificate Revocation List (CRL), which is a digitally signed list of revoked certificates and usually issued by the Certification Authority (CA). One of the shortcomings of CRL systems is that the time granularity of revocation is constrained by CRL issuance periods. It is necessary to obtain timely information regarding the revocation status of a certificate. The most popular mechanism that provides real-time status of a certificate is the Online Certificate Status Protocol (OCSP). The OCSP provides the up-to-date response to certificate status queries. Since the user just requests to return the status of certificate, the communication costs can be reduced in comparison to the CRL.
We focus on the online certification verification systems, such as OCSP and Security-Mediated PKI, and investigate the security and efficiency of these systems.

yPublicationsz
last update: 2 March 2005
[Full paper]
-
Satoshi Koga, ``A Study on Efficiency and Security of Online Certificate Verification Systems in Public Key Infrastructures,'' for master's thesis, 2005. [Abstract]
[Refereed Journal Paper]
-
Satoshi KOGA, and Kouichi SAKURAI,
``Proposal and Analysis of a Distributed Online Certificate Status Protocol with Low Communication Cost,'' IEICE TRANSACTIONS FUNDAMENTALS, Vol.E88-A, No.1, pp. 247-254, January. 2005.
[Refereed papers in conference proceedings]
-
Satoshi KOGA, Kenji IMAMOTO, and Kouichi SAKURAI,
``Enhancing Security of Security-Mediated PKI by One-time ID,''
4th Annual PKI R&D Workshop, NIST, USA, April 19-21, 2005. (to appear)
-
Satoshi KOGA, Jae-Cheol RYOU, and Kouichi SAKURAI,
``Pre-production Methods of a Response to Certificates with the Common Status,''
1st European PKI Workshop: Research and Applications (EuroPKI 2004), Samos Island, Greece, June 24-25, 2004, Volume 3093 of Lecture Notes in Computer Science, Springer-Verlag, pp.85-97, 2004.
-
Satoshi KOGA, and Kouichi SAKURAI,
``A Distributed Online Certificate Status Protocol with a Single Public Key,'' 7th International Workshop on Practice and Theory in Public Key Cryptography (PKC 2004), Sentosa Island, Singapore, 1-4 March, 2004, Volume 2947 of Lecture Notes in Computer Science, Springer-Verlag, pp.389-401, 2004.
-
Satoshi KOGA, and Kouichi SAKURAI,
``A Merging Method of Certification Authorities without using Cross-Certifications,'' In proceedings of
the 18th International Conference on Advanced Information Networking and Applications (AINA 2004), Volume 2, pp.174-177, Fukuoka, Japan, March 29-31, 2004.
-
Satoshi KOGA, and Kouichi SAKURAI,
``Decentralization Methods of Certification Authority Using the Digital Signature Schemes,'' In proceedings of 2nd Annual PKI Research Workshop,
pp.54-64, NIST, USA, April 28-29, 2003.
|
£top
|