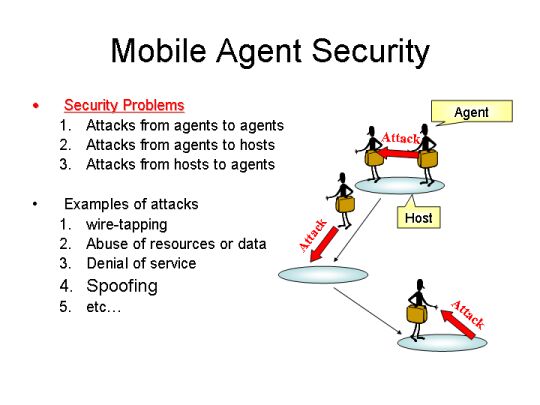
Mobile agents can perform task processing, moving through a network between hosts. Mobility can localize communication between hosts to the communication in a host, and communication cost is reducible. Mobile agent technologies are expectable as distributed processing technology of the next generation. Moreover, various agent systems have appeared by the spread of Java. When carrying out mobile agent technologies, it is necessary to consider the problem of security. Those problems can be divided into the problem which protects hosts from agents, the problem of protection between agents, and the problem which protects agents from hosts. In order to use agent technology for electronic commerce etc. actually, the technology for protecting agents from an malicious hosts is needed.
Papers
Yuki KOTEGAWA, Kouichi SAKURAI
"A Tampering Detection Mechanism using a Trusted Host for Mobile Agents",
Proc. of the 2003 International Workshop on CRYPTOLOGY AND NETWORK SECURITY (CANS2003), pp.618-623, Sep. 2003.
Yuki KOTEGAWA, Kouichi SAKURAI
"A Mechanism to Detect Tampering on Mobile Agents with Trusted Hosts",
IPSJ SIG Notes Vol.2003, No.18 pp161-166, Feb. 2003. (in Japanese)
Yuki KOTEGAWA, Kouichi SAKURAI
"Mechanism to Detect timely Alteration Attacks on Mobile Agents",
Proc. of Symposium on Cryptography and Information Security (SCIS2003), pp1193-1198, Jan. 2003. (in Japanese)