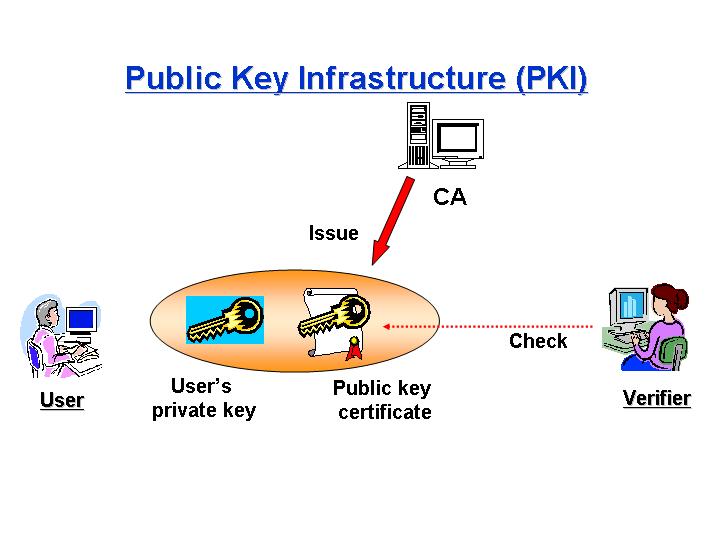
Recently, the Internet has been spread all over the world and it has used to be an infrastructure of e-commerce. However, there are several security problems on networks. Confidentiality, integrity, authentication, and non-repudiation are all security requirements. These requirements can be supported by a variety of different key management architectures. One of these architectures is a Public Key Infrastructure (PKI). In order to minimize the damage caused by CA's private key exposures, a Distributed CA (DCA) model composed of multiple CAs are required. Traditional DCAs have the problem that certification path processing is less efficient. This paper suggests a new DCA model whose path length is shorter than traditional ones. In our model, the verifier checks just one certificate and our model can mitigate the load of verifiers. To construct such model, we use a key-insulated digital signature scheme (KIS) based on the difficulity of the discrete logarithm problem.
Papers
Satoshi KOGA, Kouichi SAKURAI,
"Decentralization Methods of Certification Authority Using the Digital Signature Schemes",
Proc. of 2nd Annual PKI Research Workshop, pp.54-64, Apr. 2003,
Satoshi KOGA, Kouichi SAKURAI
"Formalization of Merger and Decentralization Mehods of Certification Authority",
IPSJ SIG Notes Vol.2003, No.18 pp155-160, Feb. 2003. (in Japanese)
Satoshi KOGA, Kouichi SAKURAI
"Decentralization Methods of Certification Authority Using Forward-Secure Digital Signature Scheme ",
Proc. of Symposium on Cryptography and Information Security (SCIS2003), pp37-42, Jan. 2003. (in Japanese)