End-to-Mobile Security in SIP
[Abstract]
Recently, the communication that uses the circuit switching technology such as
the telephone network is integrated into the IP network.
The concern for NGN(Next GenerationNetwork) that is total IP network that flexibly provides various
services has risen.
It is hoped to be able to decide parameter in communication tools flexibly between caller and callee because various terminals (cellular phone and PC) are used in NGN, and the use of various applications is assumed.
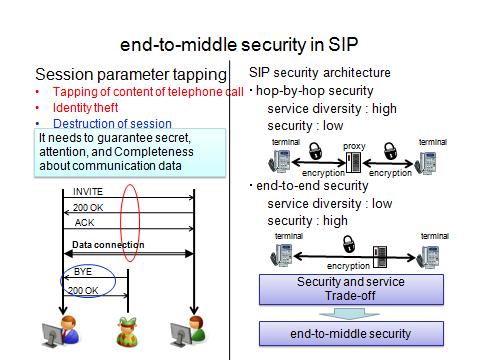
Then, it is necessary to do the communication session beginning processing that uses SIP(Session Initiation Protocol) that consults about the parameter in communication tools used among those who communicate beforehand.
However, a malicious third party can attack it by tapping SIP messages exchanged among those who communicate to establish the communication session with SIP, that is, "Other party's of the communication disguise" and "Tap of the content of the communication after the session is established", etc.
It is necessary to introduce the security mechanism to secure "The other party's of communication attestation", "Data confidentiality", and "Integrity of data" to prevent such an attack at the SIP negotiation.
[Papers]
-
白石健治、堀良彰、櫻井幸一、"SIP プロキシへの情報開示プロトコルのプライバシ評価"、平成19年度電気関係学会九州支部連合大会、沖縄、Sept. 18-19、2007.

