VM-Based Logging Scheme
[Abstract]
Logs contain actions and events that take place on a computer. Logging brings
several important benefits such as system monitoring, trouble shooting,
forensic investigation and so on. However, logging faces two threats. One is
that the logging daemon could be stopped by attackers; the other is that
existing log data could be tampered and deleted by attackers. Each threat
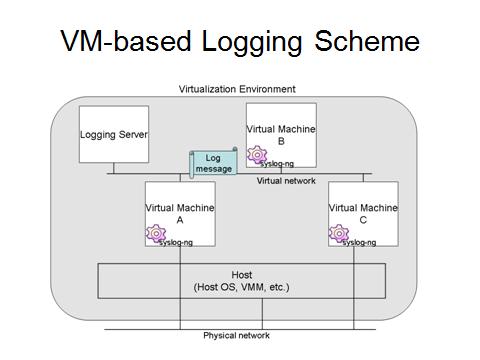
results in the loss of logs. Thus, we design a centralized and virtualized
logging scheme with the logging daemon syslog-ng which is the next generation
of syslog. The syslog application provides a secure and reliable transfer to
keep logs from tampering and deleting. The virtualization technology provides
a more secure environment by isolation to protect the logging daemon from
being shut down.
Papers
-
Bin-Hui Chou, Kohei Tatara, Taketoshi Sakuraba , Yoshiaki Hori, Kouichi Sakurai,
"A Secure Virtualized Logging Scheme for Digital Forensics in Comparison with Kernel Module Approach,"
The 2nd International Conference on Information Security and Assurance (ISA), April 2008.
-
Bin-Hui Chou, Yoshiaki Hori, Kouichi Sakurai,
"A Proposal of a Virtualized Logging Scheme under Access Control with syslog-ng,"
DICOMO 2008, 5A-4, Hokkaido, July 2008.

