RESEARCH ACTIVITIES
Nowadays, not only people but things are getting increasingly interconnected in what is called Internet of Things (IoT). In a world where almost everything is connected, if an attacker gets control of one of these networks it can be disastrous. Attacks can go as far as changing the election results of a country (USA’s 2016 election was strongly influenced by Russian cyberattacks). Moreover, in a recent report from Forbes, cybercrime is projected to reach 2 trillion dollars by 2019. To protect society, we research new technologies and paradigms for security related applications.
RESEARCH THEMES
NETWORK SECURITY
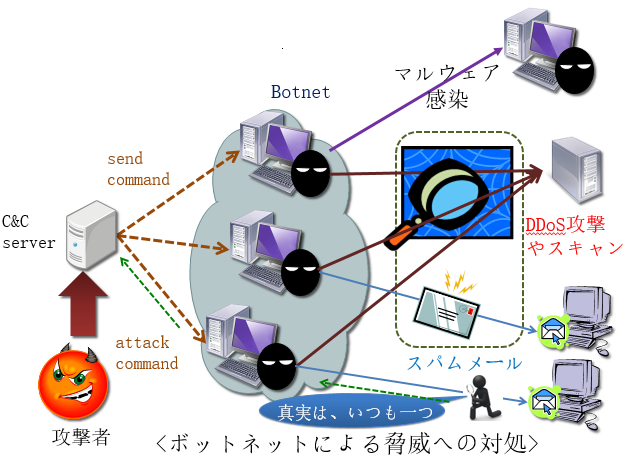
To defend attacks from malicious users we are developing learning systems that can detect cyber-attacks as well as identify anomalies, which can be new types of cyber-attacks.
Smart Security Camera
We aim to create cameras that are smart enough to identify risks or anomalies automatically. These can be done by making cameras learn to identify danger or anomalous behavior and alarm guards.

Security Robots
To aid guards we aim to develop security robots that can localize themselves and alarm guards of any suspicious behavior they find.

Adversarial Machine Learning
Learning machines are being used everywhere, however it goes often without notice that learning machines themselves can be the target of attacks. Here we analyze current systems and build new ones that are robust enough to sustain such attacks. The image below show a bus that is incorrectly identified as an ostrich by adding noisy to the image.

COMPUTER SECURITY
Malwares and other attacks sometimes can only be identified at the application layer such as suspicious access to user data, modification of computer setting among others. We aim to tackle this problem with machine learning.

Next generation cryptography and steganography
The art of encrypting messages is very important to protect privacy. For ultra-secret messages however, concealing messages is the best because the most secret message is the one that does not seem to be a message. We aim to develop new cryptography and steganography methods.
